Vpn Microsoft Remote Desktop
Deploy Windows Virtual Desktop to provide remote access for remote workers using personal devices To support remote workers who can only use their personal and unmanaged devices, use Windows Virtual Desktop in Azure to create and allocate virtual desktops for your users to use from home. Do you need to use a Virtual Private Network (VPN) along with Remote Desktop Manager? This video will show you how to quickly configure a VPN entry in order. If you create a virtual private network (VPN), you won’t have to expose the Remote Desktop server directly to the Internet. Instead, when you’re away from home, you can connect to the VPN, and your computer will act like it’s part of the same local network as the computer at home, running the Remote Desktop server. Leveraging Remote Desktop with a VPN to Control a PC Remotely on the Internet A virtual private network encrypts user network traffic to ensure that should hackers access the data they would have no way of decrypting it. The Best VPN service comes with numerous advantages for internet users. Which VPN should I use? For Microsoft Remote Desktop, use the new Campus VPN (vpn.ucdavis.edu) in most cases (though the Library VPN will still work if needed) Use the new Campus VPN (vpn.ucdavis.edu) for most purposes to access on-campus resources. (NOTE: If you need to access journals, only journals hosted on campus are accessible this way.
University faculty and staff can access their on-campus Microsoft-Windows-based computer from home another off-campus locations by using Remote Desktop.
Work computer is used in the following instructions to refer to the remote computer you wish to access. Home computer refers to the device used to initiate the remote session.
Requirements
- The work computer must be using Microsoft Windows, and must be powered on and awake. (It can be locked, and logged on or off.)
- You must have Administrator access on your work computer (contact the Help Desk if you’re unsure.)
- You must have Boise State VPN software installed and configured on the home computer.
- You must know your work computer’s computer name. (To find your computer name, type “Computer name” in the Windows search bar and select View your PC name. A Settings window will appear. Look for the “Device Name” – this is your computer name.)
- If you are using a Mac as your home computer you must download and install the latest version of Microsoft Remote Desktop from the App Store.
How to Connect with Remote Desktop
From Microsoft Windows
- Launch Boise State’s Cisco AnyConnect VPN and sign in.
- Once your VPN session is established, launch Remote Desktop Connection (select Start, type “Remote Desktop”, and run the application).
- When prompted for the computer name, enter the name of your work computer and select Connect.
- When prompted for a user name, enter your Boise State email address (e.g., BusterBronco@boisestate.edu) and password.
- You should now be connected to the work computer desktop.

How to Disconnect
- Select Start > Power > Disconnect on your work computer. This will leave your session intact so you can pick up again when you come into work, or if connect again from home.
- Disconnect your Cisco AnyConnect VPN session if you are finished.
From Apple macOS
- Launch Boise State’s Cisco AnyConnect VPN and sign in. [If you are using macOS Catalina (10.15) you may need to install the 64-bit version of Cisco AnyConnect VPN.]
- Once your VPN session is established, launch Microsoft Remote Desktop from your Applications folder.
- Select Add PC. Enter the computer name for your work computer, then select Add.
- A new entry for your work computer will appear. Double-click this entry to start your remote desktop session.
- When prompted for a user name, enter your Boise State email address (e.g., BusterBronco@boisestate.edu) and password.
- You may receive a security warning (and that’s okay). Select Continue.
- You should now be connected to the work computer desktop.
How to Disconnect
- Select Start > Power > Disconnect on your work computer. This will leave your session intact so you can pick up again when you come into work, or if connect again from home.
- Disconnect your Cisco AnyConnect VPN session if you are finished.
If your organization uses a remote access VPN solution, typically with VPN servers on the edge of your network and VPN clients installed on your users' devices, your users can use remote access VPN connections to access on-premises apps and servers. But you may need to optimize traffic to Microsoft 365 cloud-based services.
If your users do not use a VPN solution, you can use Azure Active Directory (Azure AD) Application Proxy and Azure Point-to-Site (P2S) VPN to provide access, depending on whether all your apps are web-based.
Here are the primary configurations for remote access:
- You are already using a remote access VPN solution.
- You are not using a remote access VPN solution and you want your remote workers to use their personal computers.
- You are not using a remote access VPN solution, you have hybrid identity, and you need remote access only to on-premises web-based apps.
- You are not using a remote access VPN solution and you need access to on-premises apps, some of which are not web-based.
See this flowchart for the remote access configuration options discussed in this article.

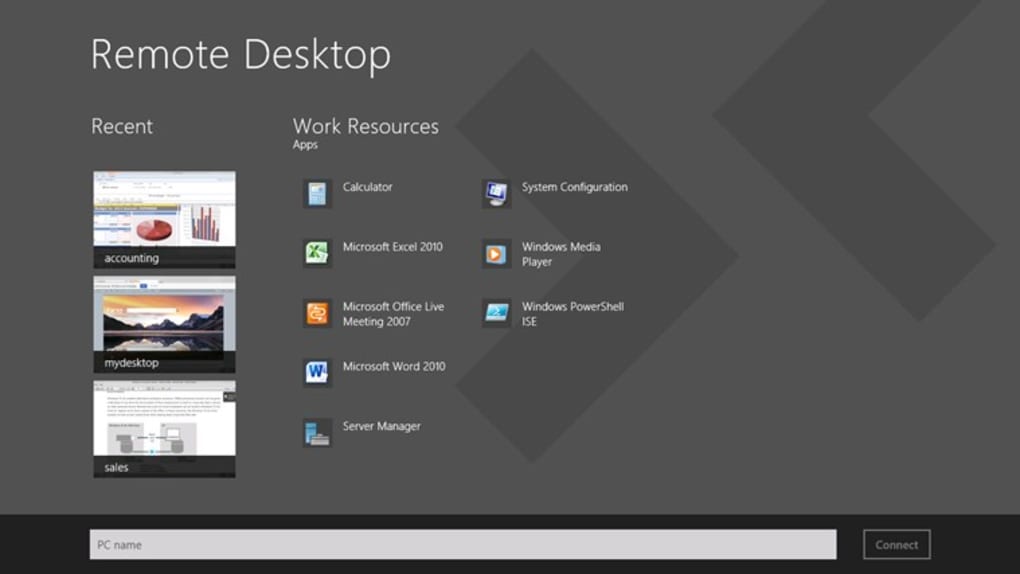
With remote access connections, you can also use Remote Desktop to connect your users to an on-premises PC. For example, a remote worker can use Remote Desktop to connect to the PC in their office from their Windows, iOS, or Android device. Once they are remotely connected, they can use it as if they were sitting in front of it.
Optimize performance for remote access VPN clients to Microsoft 365 cloud services
If your remote workers are using a traditional VPN client to obtain remote access to your organization network, verify that the VPN client has split tunneling support.
Without split tunneling, all of your remote work traffic gets sent across the VPN connection, where it must be forwarded to your organization’s edge devices, get processed, and then sent on the Internet.
Microsoft 365 traffic must take an indirect route through your organization, which could be forwarded to a Microsoft network entry point far away from the VPN client’s physical location. This indirect path adds latency to the network traffic and decreases overall performance.
With split tunneling, you can configure your VPN client to exclude specific types of traffic from being sent over the VPN connection to the organization network.
To optimize access to Microsoft 365 cloud resources, configure your split tunneling VPN clients to exclude traffic to the Optimize category Microsoft 365 endpoints over the VPN connection. For more information, see Office 365 endpoint categories. See this list of Optimize category endpoints.
Here is the resulting traffic flow, in which most of the traffic to Microsoft 365 cloud apps bypass the VPN connection.
This allows the VPN client to send and receive crucial Microsoft 365 cloud service traffic directly over the Internet and to the nearest entry point into the Microsoft network.
For more information and guidance, see Optimize Office 365 connectivity for remote users using VPN split tunneling.
Deploy remote access when all your apps are web apps and you have hybrid identity
If your remote workers are not using a traditional VPN client and your on-premises user accounts and groups are synchronized with Azure AD, you can use Azure AD Application Proxy to provide secure remote access for web-based applications hosted on on-premises servers. Web-based applications include SharePoint Server sites, Outlook Web Access servers, or any other web-based line of business applications.

Here are the components of Azure AD Application Proxy.
For more information, see this overview of Azure AD Application Proxy.
Note
Azure AD Application Proxy is not included with a Microsoft 365 subscription. You must pay for usage with a separate Azure subscription.
Deploy remote access when not all your apps are web apps
Vpn Microsoft Remote Desktop Assistant
If your remote workers are not using a traditional VPN client and you have apps that are not web-based, you can use an Azure Point-to-Site (P2S) VPN.
A P2S VPN connection creates a secure connection from a remote worker’s device to your organization network through an Azure virtual network.
For more information, see this overview of P2S VPN.
Note
Azure P2S VPN is not included with a Microsoft 365 subscription. You must pay for usage with a separate Azure subscription.
Vpn Windows Remote Desktop
Deploy Windows Virtual Desktop to provide remote access for remote workers using personal devices
To support remote workers who can only use their personal and unmanaged devices, use Windows Virtual Desktop in Azure to create and allocate virtual desktops for your users to use from home. Virtualized PCs can act just like PCs connected to your organization network.
For more information, see this overview of Windows Virtual Desktop.
Note
Windows Virtual Desktop is not included with a Microsoft 365 subscription. You must pay for usage with a separate Azure subscription.
Protect your Remote Desktop Services connections with the Remote Desktop Services Gateway
Vpn Microsoft Remote Desktop For Mac
If you are using Remote Desktop Services (RDS) to allow employees to connect into Windows-based computers on your on-premises network, you should use a Microsoft Remote Desktop Services gateway in your edge network. The gateway uses Transport Layer Security (TLS) to encrypt traffic and prevents the on-premises computer hosting RDS from being directly exposed to the Internet.
See this article for more information.
Admin technical resources for remote access
Results of Step 2
After deployment of a remote access solution for your remote workers:
| Remote access configuration | Results |
|---|---|
| A remote access VPN solution is in place | You have configured your remote access VPN client for split tunneling and for the Optimize category of Microsoft 365 endpoints. |
| No remote access VPN solution and you need remote access only to on-premises web-based apps | You have configured Azure Application Proxy. |
| No remote access VPN solution and you need access to on-premises apps, some of which are not web-based | You have configured Azure P2S VPN. |
| Remote workers are using their personal devices from home | You have configured Windows Virtual Desktop. |
| Remote workers are using RDS connections to on-premises systems | You have deployed a Remote Desktop Services gateway in your edge network. |
Next step
Vpn Microsoft Remote Desktop Login
Continue with Step 3 to deploy Microsoft 365 security and compliance services to protect your apps, data, and devices.
